Virally growing attacks on unpatched WordPress sites affect ~2m pages
Recent Situation
Attacks on websites running an unpatched version of WordPress are increasing at a viral rate. Number of defaced pages is 2 million. The reason was a serious vulnerability in the content management system came to light nine days ago. The figure represents a 26 percent spike in the past 24 hours.
Defacements have hit rogue’s gallery of site. They include conservative commentator Glenn Beck’s glennbeck.com, Linux distributor Suse’s news.opensuse.org, the US Department of Energy-supported jcesr.org, the Utah Office of Tourism’s travel.utah.gov, and many more. At least 19 separate campaigns are participating and, in many cases, competing against each other in the defacements. Virtually all of the vandalism is being carried out by exploiting a severe vulnerability WordPress fixed in WordPress version 4.7.2, which was released on January 26. In an attempt to curb attacks before automatic updates installed the patch, the severity of the bug—which resides in a programming interface known as REST—wasn’t disclosed until February 1.
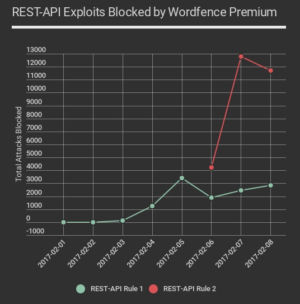
Wordfence Statistics
As shown in the graph to the right, which was provided by Web security firm Wordfence, the number of blocked attacks that attempted to exploit the bug started around February 3. The attacks steadily increased in the days following. On February 6, five days after the disclosure, number of blocked exploits were 4,000. A day later, there were 13,000. In past 48 hours, the company has seen more than 800,000 attacks across all the WordPress sites it monitors.
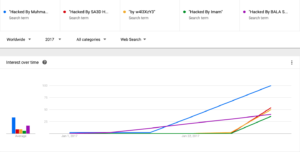
The growth roughly corresponds to this Google Trends chart, which appears directly below the Wordfence chart. It shows a spike in the number of WordPress site defacements starting around the time the vulnerability was fixed. On Thursday, the total number of WordPress site defacements measured by Google searches had increased to almost 1.5 million. By Friday, that figure had surged to 1.89 million.
“As you can see, the defacement campaign targeting the REST-API vulnerability continues with growing momentum,” Wordfence researcher Mark Maunder wrote in a blog post published Friday. “The number of attacking IP addresses has increased so, the number of defacement campaigns have increased, too.”
Competing Web security firm Sucuri has also been tracking the mass vandalism campaigns. On Friday, company founder and CTO Daniel Cid warned that attackers are releasing potentially more damaging exploits. They attempt to execute malicious code on vulnerable websites. So far, the vulnerable sites under these new attacks are those running WordPress plugins such as Insert PHP and Exec-PHP. Due to that it allows visitors to customize posts by inserting PHP-based code directly into them.
In a Nutshell
“We are starting to see them being attempted on a few sites, and that will likely be the direction this vulnerability will be misused in the coming days, weeks, and possibly months,” Cid wrote. He recommended to uninstall PHP plugins. So, the most noteworthy business at the moment for WordPress sites is to install the 4.7.2 update immediately. With the specter of code-execution attacks that can turn ordinary sites into virulent attack platforms, the health of the entire Internet is at risk.
Source: Ars Technica





